Over the years and the emergence of technology, it has been almost impossible to ignore the hyperconnectivity that exists today. This is known as the Internet of Things (ioT for its acronym in English), which is based on the interconnection of devices and objects through a network.
The IoT seeks to improve the daily life of people and companies through devices that dump the information they obtain and then share it with other devices.
Risks and threats
Just having such a large number of interconnected devices makes us think about data exposure and security in general, doesn’t it? This fear stems from the fact that by increasing connections, exposure to cyberattacks could grow.
Of course, organizations are aware of the risks and threats they are facing, in fact, 97% of companies surveyed by Microsoft, expressed their concern about security when using ioT technology. Currently there are many vulnerabilities that are unknown or not yet detected and unfortunately there are users who do not know how to maintain their security.
For example, an attack on a toaster does not seem like a problem at first glance, but many cyber attackers have the know-how to use these devices as entry points to gain access to the entire network of users’ homes.
Are there real cases similar to the previous example? Yes, it took place in 2018, where the attacker entered the Nest devices of a family (a company subsidized by Google), and managed to communicate with the victims through their baby’s monitor, just before raising the temperature of the thermostat to around 33 ° C.
After the above, we can reaffirm that the main objective of the ioT is to improve and simplify the day-to-day of companies and users, however, this technology collects our usage habits and attackers could use this information to carry out an attack.
To you who read us, we want to remind you that it is essential to be careful when entering your personal data, since with them they could carry out an attack by knowing a large part of your habits and tastes, protect yourself!
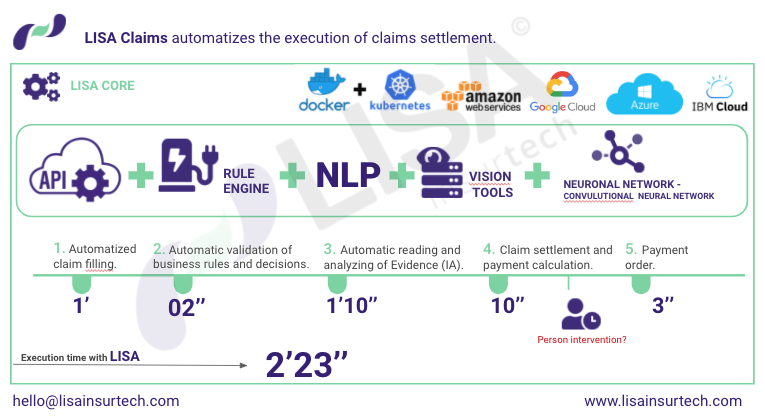
At LISA we care about the welfare and safety of insurers and their clients, which is why this article was written in order to create awareness that technology has great benefits but also has its fine print.
Therefore, we take care of using technology protected by security methods in order to avoid fraud or cyberattacks. Learn more about our work by clicking here.